Okta app for SAML and SCIM
Please reach out to your O’Reilly customer success manager to get started or if you have questions during or after configuration. They’ll connect you with a member of the O’Reilly integration team at who’ll configure the O’Reilly side of the integration while you configure your end with this guide.
Prerequisites
Please be sure you have the following before you begin updating your Okta tenant with SAML and/or SCIM.
Find and add O’Reilly’s Okta app
-
In Okta, go to the Applications admin page. Click Browse App Catalog to search the Okta Integration Network for “O’Reilly Learning Platform.”
-
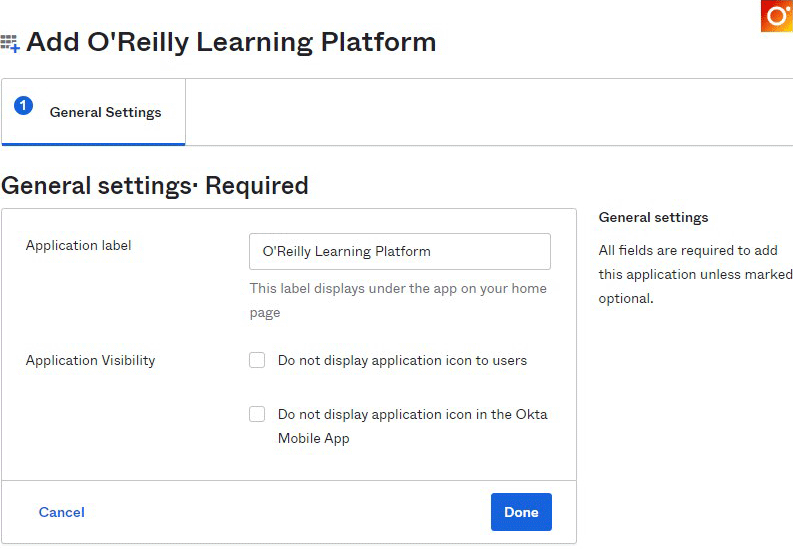
Once found, click Add Integration.
-
Change application visibility settings to hide this app if desired. (Optional)
-
Click Done to add the yet-unconfigured app to your Okta tenant. Then follow the steps below to finish setting up SAML, SCIM, or both.
Configure SAML for SSO
-
In Okta, navigate to the Sign On tab and click Edit in the top right corner. The app has been preconfigured to use SAML 2.0 as the sign-on method.
-
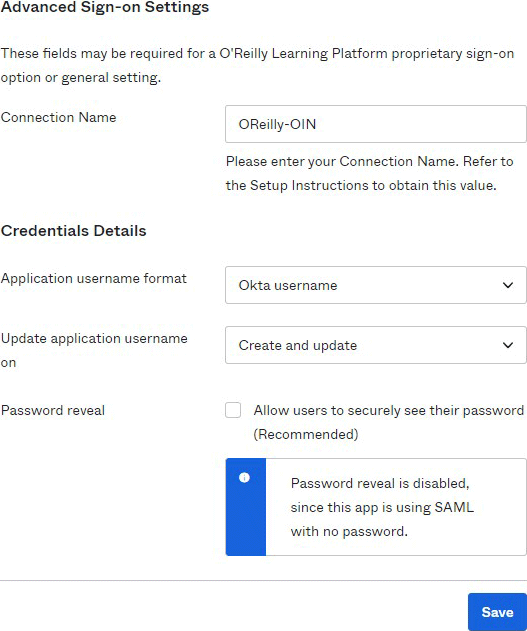
Scroll down to Advanced Sign-on Settings and enter the provided Connection Name. If you haven’t received your SSO connection name, please contact your customer success manager.
-
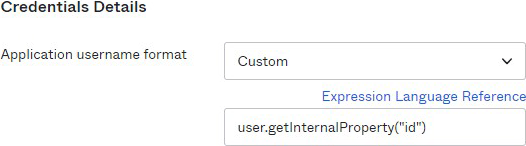
If you won’t be using SCIM with Okta for provisioning and are using Okta’s default for usernames (email), change the Application username format to be a unique and stable identifier. This allows us to automatically update users’ email addresses whenever they change in Okta. If your user directory integration does not provide a suitable identifier, we recommend Okta’s internal user profile id. To do so, select Custom and enter the following expression: user.getInternalProperty("id")
-
-
Click Save, then scroll down to SAML Signing Certificates. In the table (seen below), open the Actions menu and select View IdP metadata.
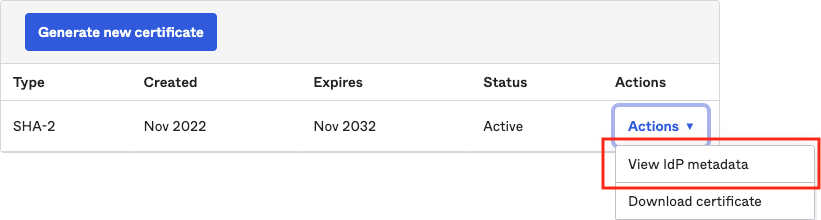
-
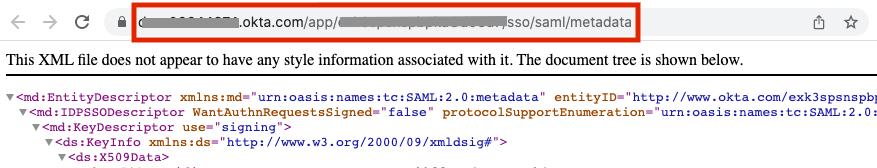
Send the URL that appears in the browser to the O’Reilly integration team at (or save the metadata XML file and email it to them as an attachment). From there, you’ll work together to test and finalize the integration. Please note that we normally disable password logins once SSO is active, so let us know if you prefer to retain password access in addition to SSO for your users.
Configure SCIM for user provisioning
Supported features
The Okta-O’Reilly learning platform SCIM integration supports the following features:
- Create Users: A user will be created in the O’Reilly platform when you assign them to the O’Reilly Learning Platform application in Okta.
- Update User Attributes: When you change a user’s name or email address in Okta, these changes will be pushed to the O’Reilly learning platform. We support the following attributes: userName, email, givenName, and familyName.
- Deactivate Users: If you deactivate a user or unassign the application in Okta, the user’s access to the O’Reilly learning platform will be revoked. This will also remove O’Reilly account manager privileges from a user who has that role.
- Reactivate Users: If you reactivate a user or reassign the application in Okta, the user’s access to the O’Reilly learning platform will be restored. Account manager privileges are not automatically restored upon reactivation; they must be requested from your customer success manager.
For more information on the listed features, visit the Okta Glossary and the O’Reilly Admin Glossary.
Known issues
None known at time of publication.
Configuration steps
-
Contact your customer success manager and request that they enable SCIM for your company to use with the O’Reilly Learning Platform OIN app. Please let them know if you plan to use SAML 2.0 single sign-on (SSO) in conjunction with SCIM user provisioning.
-
Wait for confirmation regarding your request.
-
Save the provided SCIM API Token value in your password manager or other secure location.
-
In Okta, navigate to the Provisioning application tab and click Edit.
-
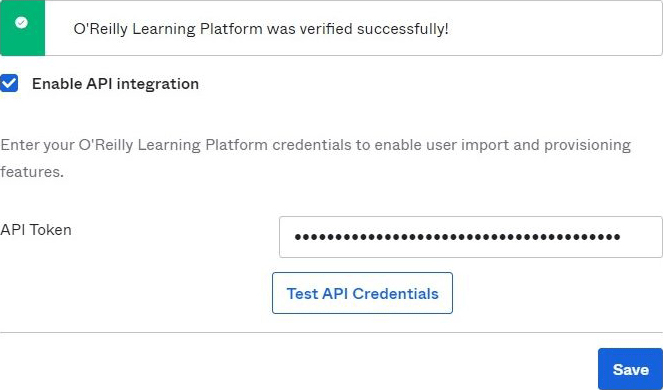
Enable the Enable API integration by checking the checkbox.
-
Enter the SCIM API Token value from step 3 into the corresponding field.
-
Click the Test API Credentials button. If you receive an error, verify that your credentials are entered correctly.
-
Upon a successful test, click Save.
-
-
Please ensure that all users who should have access to O’Reilly have been assigned this app in Okta, especially the users who are O’Reilly account managers. Continuing with the next step will remove access from any active O’Reilly users who have not been assigned this app in Okta.
-
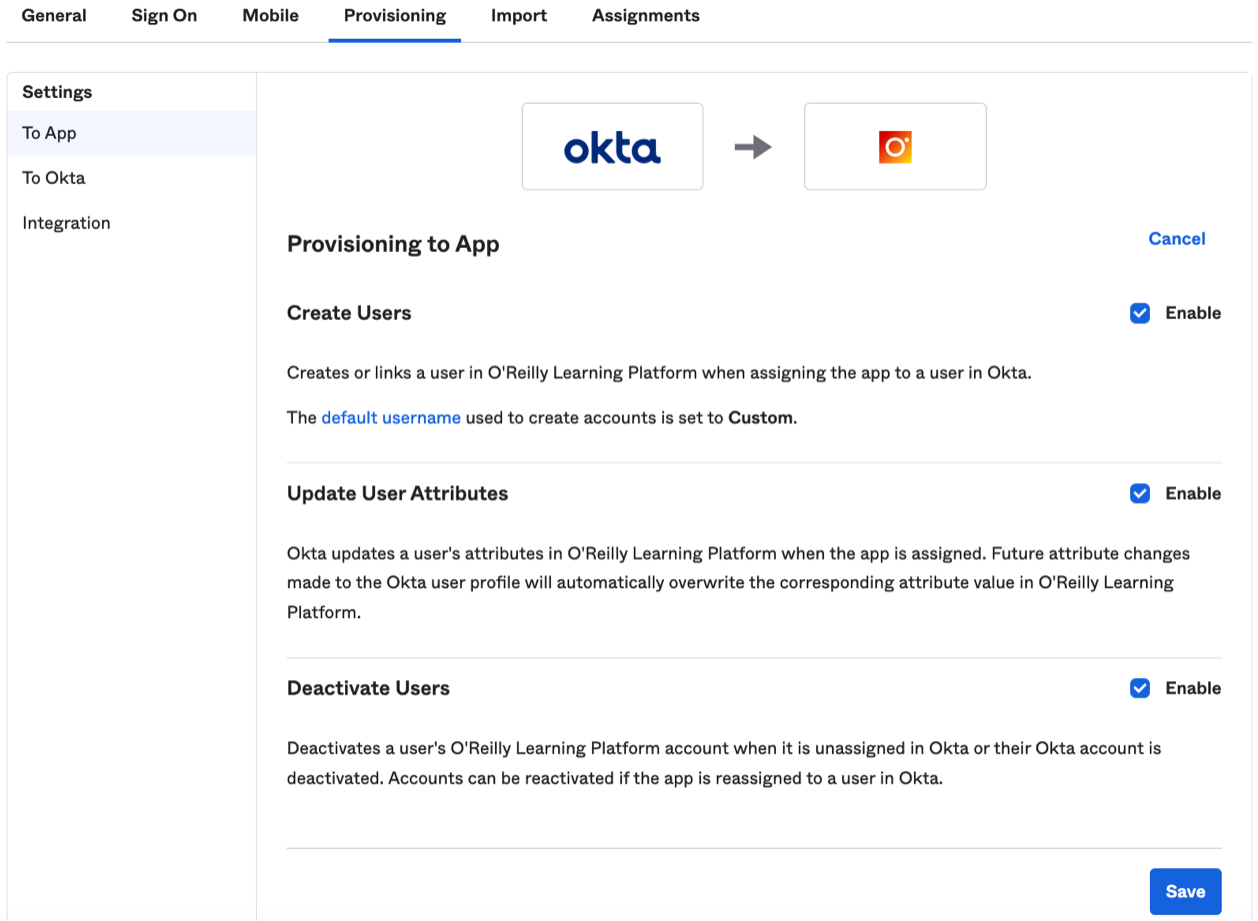
In Okta, while still on the Provisioning application tab, click To App, then click Edit.
-
Enable each provisioning operation to be used by checking the corresponding Enable checkbox, then click Save. We recommend enabling user creation, updates, and deactivation.
-
-
And you’re done! Okta now controls which users are active in the O’Reilly learning platform.
Notes
- Users who have been deactivated using SCIM will not be able to log in by any means while inactive.
- Once SCIM has been activated, managing user access by other methods can lead to discrepancies between the list of users who are assigned the O’Reilly app in Okta and the users who actually can access O’Reilly. To ensure the users assigned in Okta are the same as the users active in O’Reilly, only manage your O’Reilly access by assigning or unassigning access to users within Okta.
- Okta provides features that can help automate app assignments based on user or group information and your business rules. In addition, if Okta’s Self Service request feature is enabled, it’s possible to let users request access to O’Reilly right in Okta by configuring an approval workflow for the O’Reilly app.